Next week EclipseCon US is on.
It is going to be a busy week and Red Hat is a silver sponsor this year.
Here are some of the highlights related to Red Hat and JBoss.
Monday
CDT Summit about using Eclipse for C/C++, Linux tools etc.
Docker and Linux Tools with Jeff Johnston
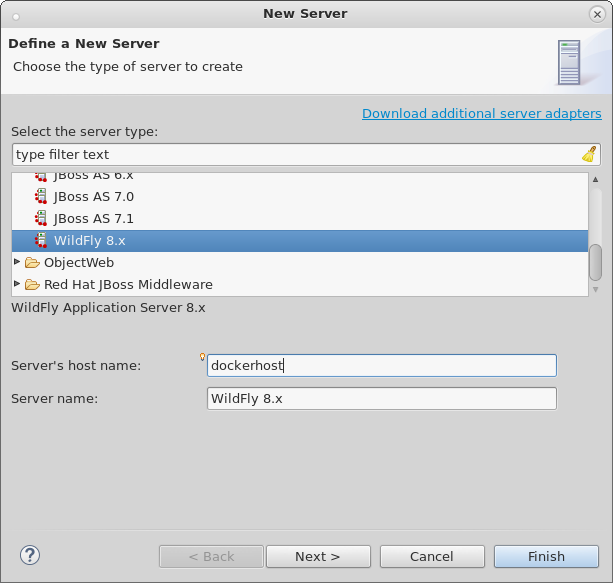
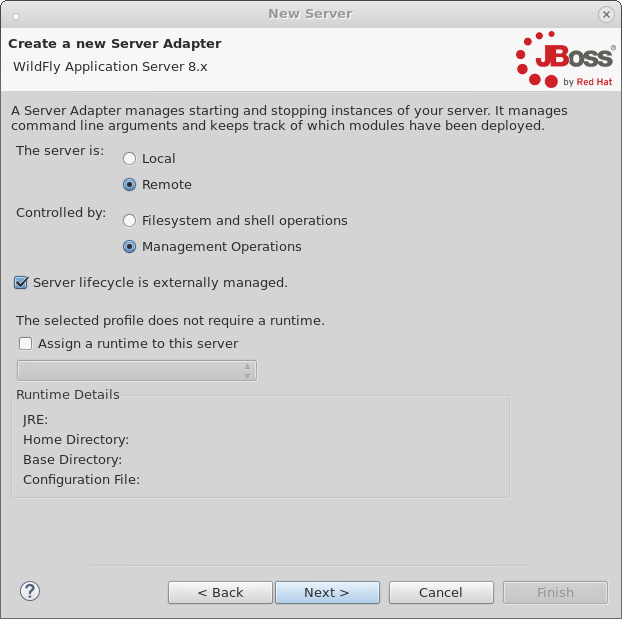
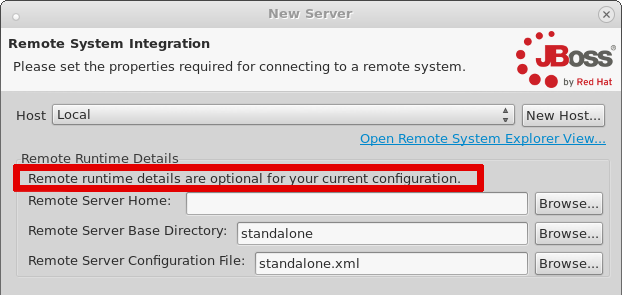
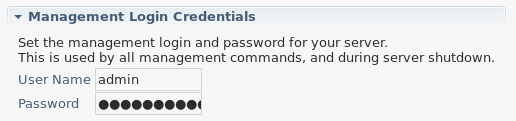
18:00 - 19:00 Docker in Eclipse - BOF hosted by Red Hat
Tuesday
Making Eclipse IDE better at handling real-life projects with Mickael Istria
Hackathon where Mickael and I will be to work on Easier & smart import of projects
Wednesday
Java EE 7 using Eclipse by Arun Gupta
Booth
Red Hat will also have a booth this year, come and say Hi!
oh..and we might have a surprise :)
Other EclipseCon
If you are near Burlinggame, SFO then be aware there are other Theme Days such as ioT, Science, polarsys and XText, these you can get into for $200.
EclipseCon is also co-loated with the FOSS4G conference if you are into location technology.
See you there!
Have fun!
Max Rydahl Andersen
@maxandersen